Please try another search. The macOS Catalina 10.15.3 update improves the stability, reliability, and security of your Mac, and is recommended for all users. The macOS Catalina 10.15.3 update improves the stability, reliability and performance of your Mac and is recommended for all users. Nov 21, 2019 GPG Suite 2019.2 - OpenPGP on macOS. Download the latest versions of the best Mac apps at safe and trusted MacUpdate.
Introduction.
When working with clients it's very common to receive and send sensitive information like server names, usernames, passwords or even client's internal information. Sharing via an email or a 'chat' program is very insecure, unless you encrypt the information using a good encryption method.
Pretty Good Privacy (PGP) is a data encryption and decryption computer program that provides cryptographic privacy and authentication for data communication. PGP is often used for signing, encrypting and decrypting texts, E-mails, files, directories and whole disk partitions to increase the security of e-mail communications. It was created by Phil Zimmermann in 1991.
The Free Software Foundation has developed its own OpenPGP-compliant program called GNU Privacy Guard (abbreviated GnuPG or GPG). GnuPG is freely available together with all source code under the GNU General Public License (GPL) and is maintained separately from several Graphical User Interfaces (GUIs) that interact with the GnuPG library for encryption, decryption and signing functions. One of those GUI is GPG Tools. This tool is the one we are going to explain here so we'll be able to encrypt text in Mac OS X.
GPG encryption works by generating a key pair: a private key and a public key. The public key is the one you give to other people, then they will use your public key to encrypt messages they want to send to you. When you received a message encrypted with your public key there only one way to decrypt it: using your private key. There's no way to decrypt the message with any other key (private or public), that's the reason it's called 'key pair'. And just to be clear, there's no way to infer, guess or obtain your private key from your public key.
Installing GPG Tools.
Go to the GPG Tools website and download the GPGTools.
Close 'Mail' before continue. Open the .dmg file you just downloaded and double-click on the installer 'GPGTools.mpkg' file.
Follow the instructions of the installer to complete the installation.
Generating the private and public keys.
Open the GPG Keychain application which should be located in you Mac Applications folder.
In the application's main window click the 'New' button, it has a key icon and it's the first button on the left in the toolbar.
In the 'Generate new key pair' window type your name and email address. Your email address must be the same you have configured in Apple Mail program. If you do not use Apple Mail program then just type your email but use your actual email address and not an alias.
Click the 'Generate' button and it will ask you for a passphrase. A passphrase is like a password but more secure, it can include spaces and it's usually longer than a password.
IMPORTANT
If you have a photographic memory then memorize your passphrase or store it in a secure place. If you forget your passphrase you won't be able to recover it, at least not in your life time. Yes, it's that secure.
After you type your passphrase, move your mouse pointer while it's generating the key pair, the program will use mouse movement and other information from processes running in the computer to generate a more secure key. After the process finish you will have your key pair generated.
Sharing your public key.
To make PGP useful you need to share your public key with others so they are able to encrypt information that is only for you. To do this you go back to the main window of the 'GPG Keychain Access' program, then you right-click the key you want to share and select 'Export..'. After that you will get a 'Save as..' dialog, choose a name and a folder where you want to save the public key.
Now you just have to send this file to others, they'll just need to import the file by clicking the 'Import key' button in the toolbar of the main window and select the public key file.
Enable text encryption.
To enable the encryption of text we will use Mac OS X Services so any application that uses Services will have the ability to encrypt text, like in the TextEdit editor that comes with Mac OS X.
Go to System Preferences --> Keyboard, select the tab 'Keyboard Shortcuts' and then select 'Services' in the list on the left. In the list on the right look for the following services under the 'Text' section and mark their check boxes:
- OpenGPG: Decrypt Selection
- OpenGPG: Encrypt Selection
Encrypting text.
To encrypt text, open the TextEdit editor (or any other application using Mac OS X 'Services'), type the text you want to encrypt and select the text, then click on the 'OpenGPG: Encrypt Selection' command from the Services submenu, and select the public key you want to use for encryption which must be the public key of the person you are sending the encrypted information to. In the images below we're using encrypting the text for the GPGTools Project Team.
After the encryption you will end with the encrypted text that will look similar to the following image.
Decrypting text.
To decrypt text you can copy and paste the encrypted text into the TextEdit editor, select all the text and do the reverse process: Click the 'OpenGPG: Decrypt Selection' command in the Services menu and the GPGTools will decrypt the text using your private key.
The following assumes you are using gnupg2 with macports, and not MacGPG2, but the fix will likely apply to your use case. Install 'pinentry' package from macports: port -v install pinentry Edit your /.gnupg/gpg-agent.conf to suit: pinentry-program /opt/local/bin/pinentry-curses Remove or comment the existing 'pinentry-program' entry. Reload your terminal, or use this: echo RELOADAGENT gpg-connect-agent Done. You should now have pinentry/passphrase in-terminal (curses dialog). If you wish to have the old gpg v1.x behaviour of inline-ttl pinentry, you may be able to use a custom './configure' command with the macports pinentry package.
GnuPG is a complete and free replacement for PGP. Because it does not use the patented IDEA algorithm, it can be used without any restrictions. GnuPG is a RFC2440 (OpenPGP) compliant application.
If you have previously installed MacGPG2 / GPG tools for Mac, you may need to kill the 'shutdown-gpg-agent' process before the pinentry dialog will work (or just reboot). User$ ps ax grep shutdown-gpg-agent 1854?? S 0:00.01 /bin/bash /usr/local/MacGPG2/libexec/shutdown-gpg-agent user$ kill -KILL 1854. I just finished compiling the GnuPG (version 2.2.9) and all its dependencies for a Mac OS High Sierra. It was quite interesting. After solving a small problem with the tests of libgcrypt (with a little help of the respective recipe from Homebrew), everything worked basically out of the box.
While trying to import my private key, I couldn't, because the system was lacking a pinentry program. A quick search made me land on this page, but it wasn't very helpful, so I simply decided to compile the pinentry myself. I already knew, from my experience using GnuPG on Linux machines, that I would like to type my password in a normal prompt on the command line, without those annoying, disrupting dialog boxes. And that's why I'm sharing the process here. It's simple, but might help someone with a similar problem.
Start by getting the source code of pinentry from GnuPG. At the time of writing, the link to download the source was. Download also the and check the authenticity using gpg itself. DON'T SKIP THE VERIFICATION, this is important! This program will have access to all your gpg passwords and private keys. You better make sure it is what it claims to be! If you have problems, make sure you have imported the keys from the maintainers of GnuPG (see ): $ gpg -verify pinentry-1.1.0.tar.bz2.sig pinentry-1.1.0.tar.bz2 Now that you are sure you are working with authentic source files, extract the source code and cd in that directory: $ tar xvf pinentry-1.1.0.tar.bz2 $ cd pinentry-1.1.0 The compilation is very straight forward: $./configure -enable-pinentry-tty $ make $ sudo make install It might be that configure will complain about some missing dependency.
It that case, simply read the error and download the dependency from GnuPG webpage (always checking for the integrity of the download!). The important bit of the commands above is the flag -enable-pinentry-tty. Pinentry TTY is the simplest way to type your password in a very normal and boring prompt on the command line. Exactly what I wanted! If I'm not mistaken, the curses version will be built anyways. Although it's a CLI option, I find it as disruptive as all the others. Once it's installed, you will see some new binaries in /usr/local/bin.
Make sure you have one called pinentry-tty (if you don't, something went wrong.). To make that new binary your default way of typing the gpg password, add the following line to /.gnupg/gpg-agent.conf (create the file and directory if they don't exist yet): pinentry-program /usr/local/bin/pinentry-tty It won't probably work if you try immediately, because you most likely still have an gpg-agent running with old configuration. Go ahead and kill all the gpg-agents and create a new one: $ sudo killall gpg-agent $ gpg-agent -daemon That's it! Enjoy you old-style TTY pinentry:).
Glad you made it here and thanks for your interest. In this article you'll learn how to setup your own GPG key and send your first secure email. Setup GPG Suite The first step is to download and run. When that is done, it's time to setup your GPG key. If you already have a GPG key, please, because in that case you don't need to create any new key. If you do not have a GPG key yet, follow up with the next section: Create a new key GPG Keychain is the application you will use to manage your keys.
It will let you create new keys, edit existing ones and search for your friends keys. The first thing you'll see in GPG Keychain is a wizard which will guide you through creating your first key.
Email Address GPG Keychain fills the data from your OS X address book. But the fields are editable and you can change them at your will.
Enter the email address you normally use when sending mail. Make sure that it is typed identical to the one used in Mail.app Preferences Accounts. Double check that capitalisation matches, since it matters. More email addresses can be added to your key later. Upload key after generation If you enable this checkbox, your public key will be uploaded to a key server once key creation is done. Generally this is a good thing, since it will make it much easier for others to start sending you encrypted messages by simply importing your key from a key server, but once a key is uploaded to the key server, it can not be removed.
This means: you will not be able to change your name once the key has been uploaded. You can always upload your public key to a key server at a later time. Password Enter your password. As with every other password you use, it should be very strong and it's best to use a very long password,a sentence you can remember, comprised of symbols and numbers.
Important: Should you forget your password, there's no way to recover it. Make sure you will remember it or store it in a safe place (no, a text note on your desk is not a safe place). Hit 'Generate key'! After a short while, you'll see a new entry in GPG Keychain with your email address showing sec/pub (secret/public) in the type column. Every time you create a new key, a new key pair is created. It will consist of a secret key and a public key.
The public key is to be shared with others, so they can send you encrypted messages. Important: If you delete your secret key, you will no longer be able to read encrypted messages. Add your address used in Mail.app to an existing GPG key To send encrypted emails with Mail.app using GPGMail, you have to add the address used in Mail.app to your existing GPG key. If you are 100% certain that the address used in Mail.app is already setup in your existing GPG key, then you can get started with creating:. Otherwise add your email address as User-ID to your existing key. Double-click the sec/pub key, to which you want to add a User ID. 2.
Key details will open - select the 'User IDs' tab. 3. Click the '+' to add another email address as User ID. 4. A dialog opens in which you enter Name and email address, we recommend to leave the comment field blank.
5. Click 'Generate User ID'.
6. Pinentry will ask for your password Repeate the above steps to add as many User IDs as you need.
Since you now have several User IDs, it is recommended to set the most commonly used address as primary User ID. To do that:. 1. Select the User ID you want to set to 'Primary'.
2. Click the cogwheel (next to the '+'). 3. Select 'Primary' Important: If your key is on the key servers, don't forget to upload your updated key via menu Key Send to Keyserver ( ⇧⌘K). Otherwise the change will only be local and your contacts can't benefit from the new User IDs. Your first encrypted mail Great, you're almost there! All you need for this first test is a sec/pub key in GPG Keychain matching the mail address used in Mail.app.
If you want to encrypt to other recipients than yourself, you need to retrieve their public key first. On macOS 10.14 Mojave you need to. This is a new mechanism Apple introduced in 10.14.
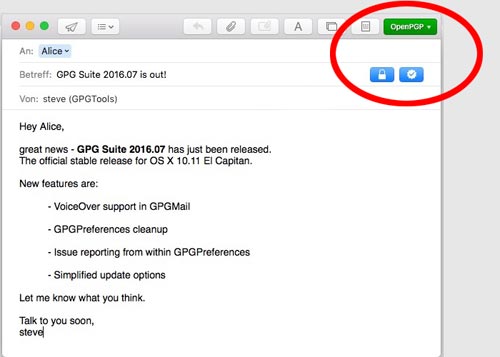
Open Mail.app and create a new message. You'll notice two additional buttons in your composing window. A lock icon for encryption and a star icon for the signature. For both icons: grey means disabled, black means enabled.
As you have just created a key, your star icon will be enabled. You are now ready to sign messages with your key. After you click the star icon you will see a check mark indicating that your message will be signed.
Your lock icon however will be displayed in grey as you must first enter a recipient, for whom you have a public key. For this test: enter your email address in the 'To:' field (the same address that you use to send emails from).
Then your lock icon will change to black. You are now ready to encrypt your message. Click to close the lock. Your mail will now be encrypted. After pressing the lock or star button, the OpenPGP indicator in the top right corner will turn green. This indicates that your mail will be signed and/or encrypted.
Gpg Tool
Your email should look like this: The OpenPGP indicator is green, the lock icon is locked, your message will be encrypted and a small checkmark is displayed on the star button (the message will be signed). Download portrait professional activation token keygen mac. Press send: If your password is not stored on your computer you will be asked to enter it manually (in order to sign the message).
Shorty, the mail will be delivered to yourself. You'll see that it is encrypted and signed: the lock is closed, indicating that the message was encrypted and since you can read the mail-content, it has been successfully decrypted for you. If you don't see the lock icon the message wasn't encrypted.
Mail.app Preferences GPGMail allows to adjust the defaults for encrypting and signing new mails. Congrats, you've made it!
To be completely honest we have to admit, we've cheated a little. Encrypting a message can be slightly more effort, since it requires you to have the public key of the recipient(s). However adding their public keys is a task that you only do once for each recipient. How to find your friend's public key If your friends don't already have a key-pair of their own, they need to create one.
Download From Security Camera To Flash Drive
If they are not on OS X and able to use GPG Suite we recommend for Windows and for Linux. After key creation, the public key should be uploaded to a key server. Also in order for your friend to be able to encrypt or sign messages, they need to use a mail client with an OpenPGP plugin - analogue to using Mail.app with the GPGMail plugin.
open GPG Keychain. press cmd ⌘ + F and enter the email address or your friends name. press 'Search key' If a public key for your search terms exists on the keyserver, you should see something like the following: Select the keys you want to import by clicking their checkboxes and press 'Retrieve key'. Then start Mail.app and write the first encrypted mail to your friend as you learned in Why all this hassle? First, sending an encrypted message isn't more difficult than sending unsecure messages, once you've understood the basic concept. Second, by sending encrypting messages you will prevent unwanted eyes (NSA) from reading the contents of your personal mails. Third and this might not be as clear: why should you sign messages?
You can compare signing a message to the process of sending a sealed letter in real life. For one, the recipient will be able to tell if the 'seal' was broken. If anyone has been fiddling with your message your recipients will immediately see that the signature is invalid.
On the other hand, they can also be sure that the message did indeed come from you and not an imposter, since only you can create that signature, with your secret key. One could fake your email address, your name, but not your signature. And that's why signing is important. This also explains why it's EXTREMELY IMPORTANT to keep your secret key and your password safe. Otherwise, if someone gets a hold of your secret key and your password, they could forge your signature and pose as you.
In addition, they could read your encrypted messages, and you really wouldn't want that. Further info. Watch. Read up on. your keys. Setup encryption on a. to your key.